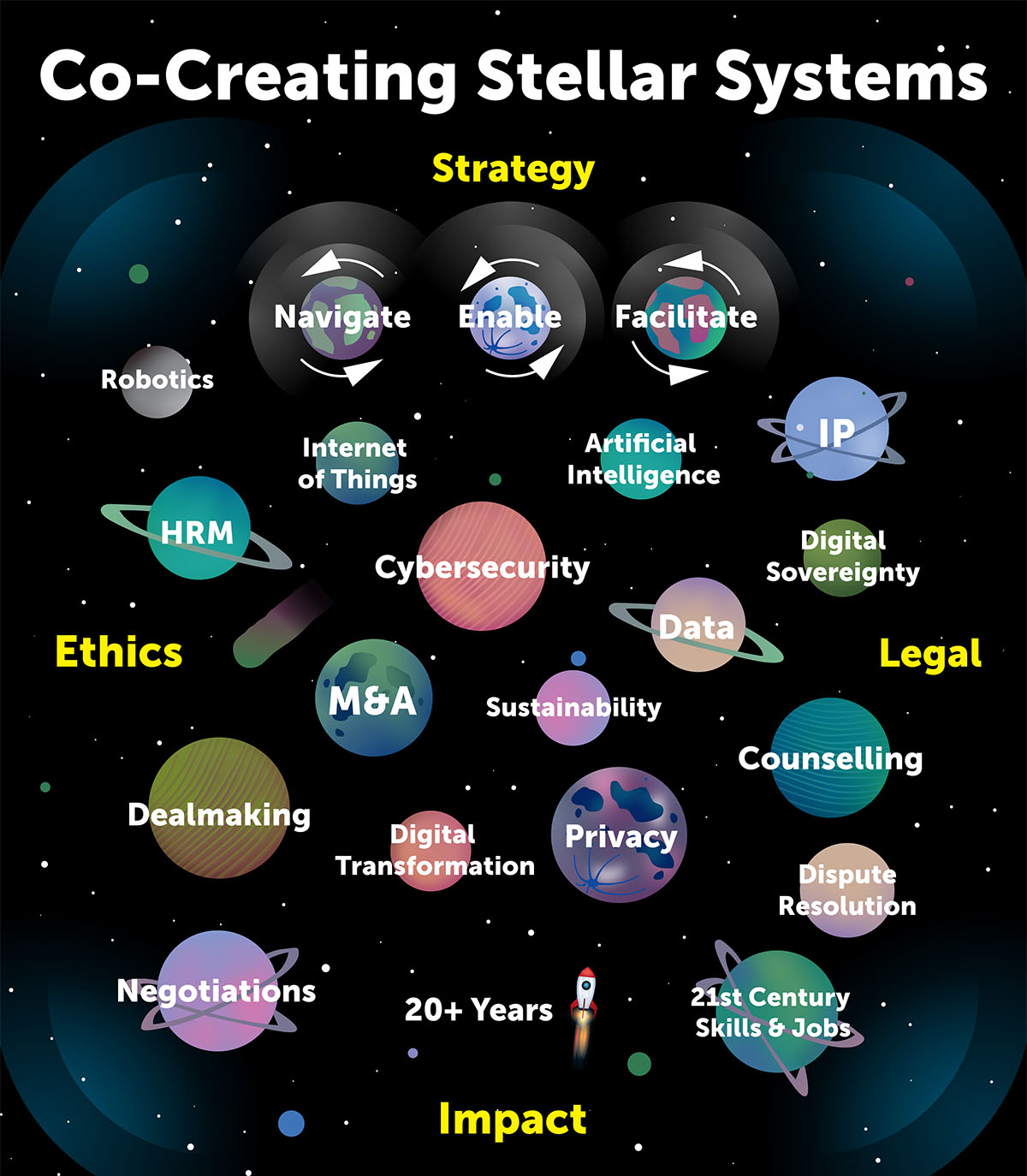
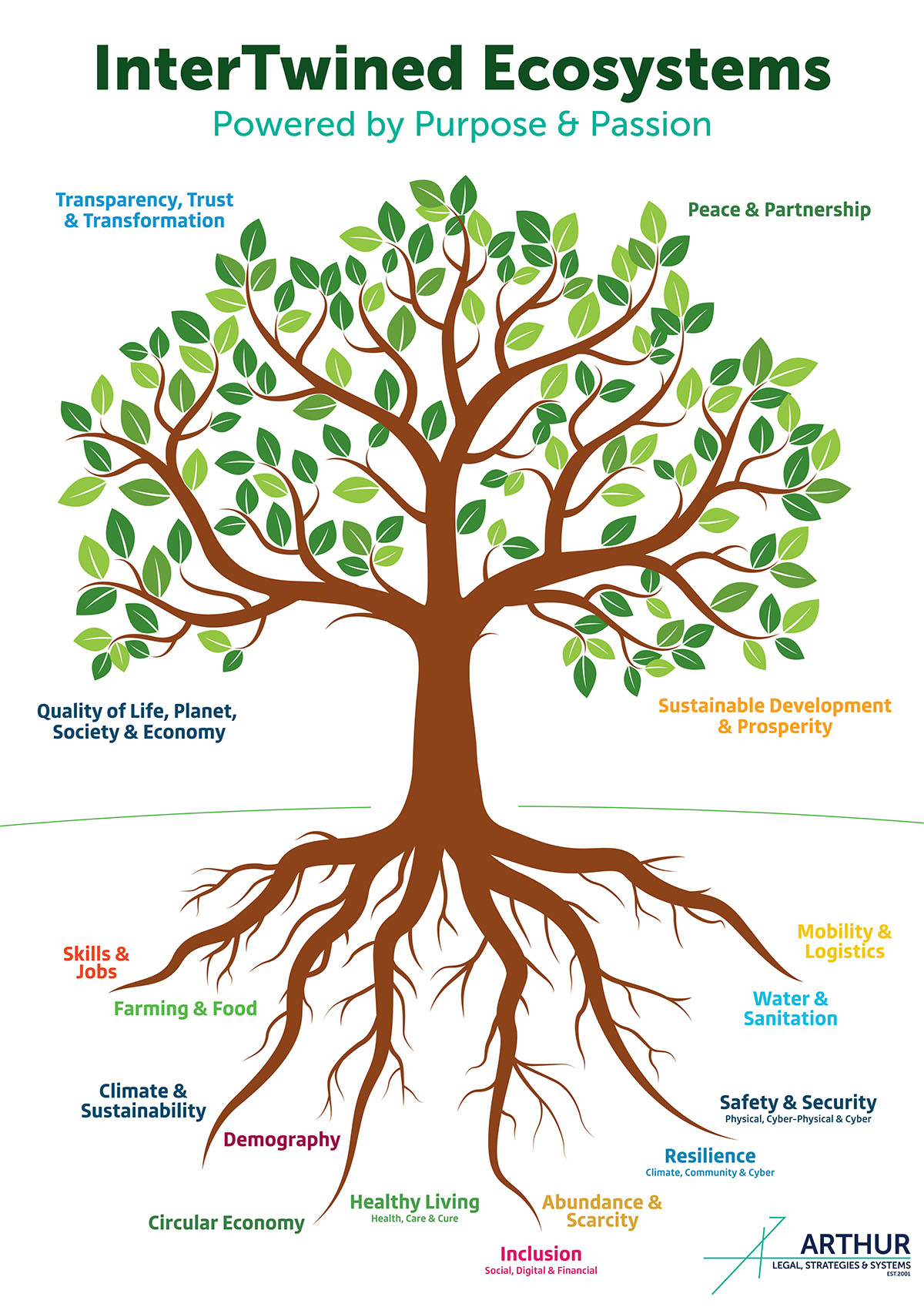
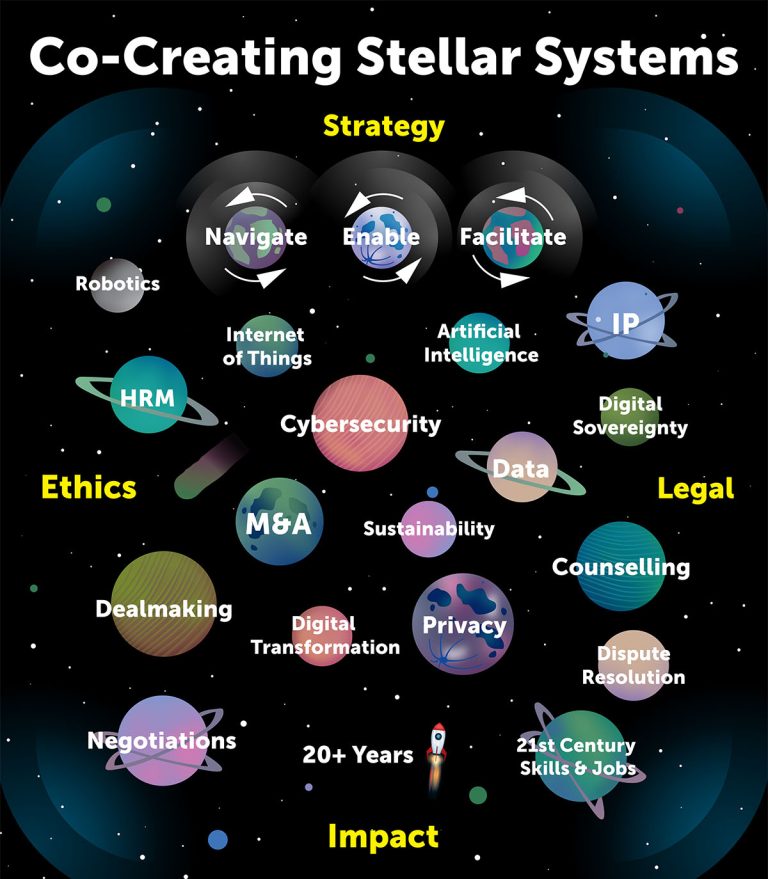
Strategy
Building resilient systems for a complex, digital world
ARTHUR’s Strategies & Systems helps organisations navigate a world that is becoming ever more complex, digital, and interconnected. Inspired by Von Humboldt’s vision of interdependence, we build resilient ecosystems where human insight, technology, and trust converge to create future-proof solutions. Collaboration is at our core.